Maybank2U Graded 'F' Compared To Other Online Banking Sites in Malaysia
It's hard to imagine life without the convenience of online banking - it's instant, queue-free and secure… right? You may be shocked at some security information BolehVPN dug out recently.
Maybank2U And Maybank2E Joins Top Ranks While BSN, Affin And Muamalat Remain Lowest Graded Banking Sites in Malaysia
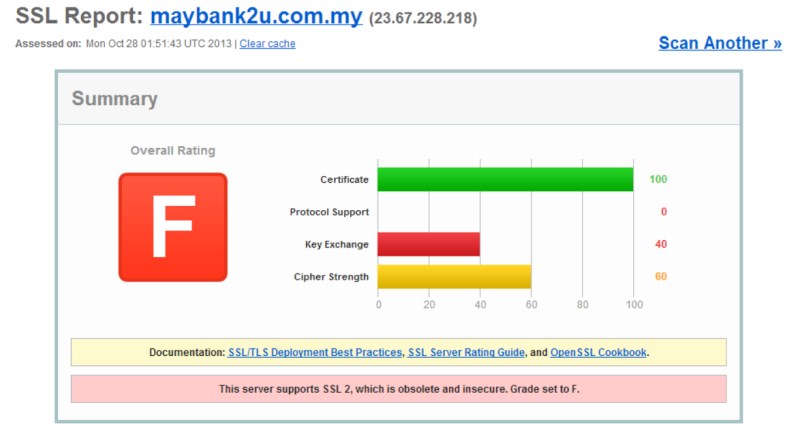
Earlier this week, a HTTPS security test session on local online banking services by a local VPN provider BolehVPN have gained attention from many users due to the F grade rating that were given to a number of the services in the test. These services include the hugely popular Maybank2U as well as its enterprise counterpart Maybank2E together with AffinOnline, i-Muamalat and myBSN.
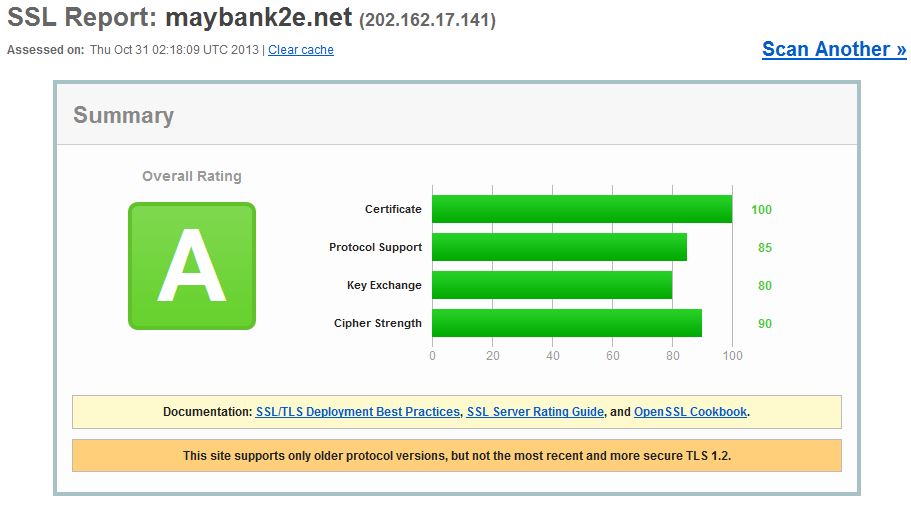
lowyat.netWhile HTTPS security is just one of several security methods (an important one, nevertheless) that banks have implemented over their online bank services, the results raised concerns among a lot of users. So, here’s a great news for Maybank customers out there: Maybank2U and Maybank2E are now rated with the A grade by SSL Labs’ tool that BolehVPN used in their test.
bolehvpn.netHowever, the same thing can’t be said about AffinOnline and i-Muamalat as their SSL Test grade still remained at F. That being said, AffinBank have responded to our query with their take on the test results in which we will discuss in subsequent post. As for myBSN, the test is not able to resolve the domain name as of 950pm due to unknown reason.
lowyat.netBolehVPN looked at HTTPS vulnerabilities and analysed Malaysia’s top banks like Maybank2U and CIMB Clicks. The results that came out are shocking.
A local VPN service provider, BolehVPN earlier today have posted a rather interesting blog post regarding a test that they have recently done to nine online banking services that are operated by Malaysian-based banks.
lowyat.netUsing an automated test by Qualys SSL Labs, the good news is that majority of the test subjects are graded as A by the test which runs deep analysis on the configurations of a SSL-equipped web server.
bolehvpn.netMaybank2U has been graded 'F' due to its support for SSL 2.0 which is said to be obsolete and insecure.
It's probably the most used Online banking facility and shockingly, it scores a 'F' due to its support of SSL2.0 and weak ciphers. Their site also does not implement forward secrecy.
bolehvpn.netMaybank2E, meant for ‘enterprise customers’ is even worse with a whole plethora of security issues. It was graded 'F'.
It supports insecure renegotiation which allows MITM attacks. In fact, we can test this out by just logging into Maybank2E using IE. Even after several days of leaving it idle, forcing a refresh still allows you to access all data.
bolehvpn.netIt is also vulnerable to DOS attacks due to its support of client-side re-negotiation. Thankfully it does not fall into the same mistake as Maybank2U and does not accept SSL2.0. It however still accepts weak antiquated ciphers.
lowyat.netIronically, Maybank2E received an award for Best Ecommerce Bank and Best Transaction Bank in Malaysia in 2011
CIMB Bank along with Public Bank both received 'A'
Public Bank is reasonably secure but is not as good as CIMBClicks due to its support of TLS version 1.0 only. Also it’s also potentially vulnerable to Denial of Service attacks due to its support of client-side re-negotiation.
bolehvpn.netHong Leong also scored well though it only supports TLS version 1.0 and not the more secure 1.1 and 1.2. And, it’s the same story with UOB Malaysia. Reasonably good security but no support of TLS 1.1 or 1.2.
bolehvpn.netRHB Malaysia, on the other hand, did not yield any grading. Upon testing it returned the following error: “Assessment failed: No secure protocols supported”.
Alliance Bank received 'A' in the grading. But it doesn't support secure re-negotiation and latest TLS.
Alliance Bank received 'A' in the grading. But it doesn't support secure re-negotiation and latest TLS.
Image via wikimapia.orgAffin Bank received 'F' and proved another failure. It scored a score of 0 out of 100 for protocol support.
Also, like Maybank2E it is vulnerable to MITM attacks because it supports insecure renegotiation and is easier to attack via DoS because it supports client-initiated renegotiation.
bolehvpn.netThe site is also intolerant to newer TLS protocol versions, which might cause connection failures and has compatibility issues with modern browsers. Obviously, their online banking system hasn’t been updated in a while.
bolehvpn.netStandard Chartered Malaysia is another site to get 'A'. Well done, SC.
Good marks all around. However unlike CIMBClicks, it does not implement server-side BEAST mitigation. However, it implements proper session resumption which CIMBClicks doesn’t.
Image via wikimedia.orgAlthough, Bank Islam received 'A', there is something confusing about the site
Going to their main website there’s a warning that tells you to access it through www.bankislam.com.my only. However, when clicking on the Internet Banking link, it redirects you to bankislam.biz
bolehvpn.netIt appears to be legit but the contradicting instructions does raise worries if it is indeed an official site especially since most banking websites don’t use .biz.
bolehvpn.netBankislam.biz shows decent HTTPS security but is intolerant to newer TLS protocol versions, which might cause connection failures and has compatibility issues with modern browsers. It also disables secure renegotiation and does not mitigate the BEAST attack.
bolehvpn.netOCBC and CitiBank both received 'A', showing strong results
OCBC showed similar results to Standard Chartered. No serious weaknesses beyond no BEAST server side mitigation.
bolehvpn.netCitiBank too showed similar results to Standard Chartered. No serious weaknesses beyond no BEAST server side mitigation. Slight anomaly in which citibank.com.my resolves differently than www.citibank.com.my but should be ok.
bolehvpn.netAmBank, Bank Muamalat, Bank Simpanan Nasional and Bank Rakyat all graded 'F'
AmBank only scores a B due to its support for 56 bit TLS_RSA_WITH_DES_CBC_SHA cipher. It is also vulnerable to DoS attacks due to it supporting secure client-initiated renegotiation.
bolehvpn.netBank Muamalat received 'F'. Similar to Maybank2E. Allows insecure client initiated renegotiation that increases chance of MITM attacks. It’s also more vulnerable to DOS attacks.
bolehvpn.netAnother big failure was Bank Simpanan Nasional which also got 'F'. Allows insecure client initiated renegotiation that increases chance of MITM attacks. It’s also more vulnerable to DOS attacks.
bolehvpn.netBank Rakyat saved some face by getting a 'B'. But that's only due to their support of the 56 bit TLS_RSA_WITH_DES_CBC_SHA cipher. It is also vulnerable to DoS attacks due to it supporting secure client-initiated renegotiation.
bolehvpn.netOverall, only CIMBClicks, Standard Chartered Bank, CitiBank and OCBC showed excellent HTTPS security. So, what is HTTPS security anyway?
Hypertext Transfer Protocol Secure (HTTPS) is a communications protocol for secure communication over a computer network, with especially wide deployment on the Internet.
Technically, it is not a protocol in and of itself; rather, it is the result of simply layering the Hypertext Transfer Protocol (HTTP) on top of the SSL/TLS protocol, thus adding the security capabilities of SSL/TLS to standard HTTP communications.
The encryption within HTTPS is intended to provide benefits like confidentiality, integrity and identity. Your information remains confidential from prying eyes because only your browser and the server can decrypt the traffic. Integrity protects the data from being modified without your knowledge
A site must be completely hosted over HTTPS, without having some of its contents loaded over HTTP, or the user will be vulnerable to some attacks and surveillance. For example, having scripts etc. loaded insecurely on an HTTPS page makes the user vulnerable to attacks. Also having only a certain page that contains sensitive information (such as a log-in page) of a website loaded over HTTPS, while having the rest of the website loaded over plain HTTP will expose the user to attacks.
On a site that has sensitive information somewhere on it, every time that site is accessed with HTTP instead of HTTPS, the user and the session will get exposed. Similarly, cookies on a site served through HTTPS have to have the secure attribute enabled.
What is SSL and what are Certificates?
Secure Sockets Layer (SSL) are cryptographic protocols which are designed to provide communication security over the Internet. They use X.509 certificates and hence asymmetric cryptography to assure the counterparty whom they are talking with, and to exchange a symmetric key.
globalsign.euThis session key is then used to encrypt data flowing between the parties. This allows for data/message confidentiality, and message authentication codes for message integrity and as a by-product message authentication.
SSL Certificates are small data files that digitally bind a cryptographic key to an organisation’s details. When installed on a web server, it activates the padlock and the https protocol (over port 443) and allows secure connections from a web server to a browser.
What is 'Forward Secrecy', the feature that was reportedly lacking in Maybank2U and CIMB Clicks?
With revelations about mass surveillance in the news everywhere, an obscure feature of SSL/TLS called 'Forward Secrecy' has suddenly become very interesting. So what is it, and why is it so interesting now?
Every SSL connection begins with a handshake, during which the two parties communicate their capabilities to the other side, perform authentication, and agree on their session keys.
ivanristic.comThe session keys are then used to encrypt the rest of the conversation (session), possibly spanning multiple connections. They are deleted afterwards.
The goal of the key exchange phase is to enable the two parties to negotiate the keys securely; in other words, to prevent anyone else from learning these keys.
ivanristic.comSSL supports forward secrecy using two algorithms, the standard Diffie-Hellman (DHE) and the adapted version for use with Elliptic Curve cryptography (ECDHE).
Why isn't everyone using them, then?
Assuming the interest and the knowledge to deploy forward secrecy are there, two obstacles remain: DHE is significantly slower. ECDHE too is slower, but not as much as DHE.
ivanristic.com