[NEW UPDATE] Facebook Says They Should've Listened to Khalil
The Palestinian hacker who broke into Mark Zuckerberg's Facebook Timeline to call attention to a bug he discovered will get at least $11,000 as a reward — not from Facebook, but from an online crowdsourced campaign.
Facebook hacker, Khalil Shreateh, awarded $11,000 by crowdsourced campaign
The Palestinian hacker who broke into Mark Zuckerberg's Timeline will get $11,000 from a crowdsourced campaign, after Facebook refused to reward him.
Palestinian hacker Khalil Shreateh who hacked Zuckerberg’s Facebook account to be rewarded with $12,000 - The Hacker News
Facebook says they should've listened to Khalil
Facebook acknowledged the company should have listened to the Palestinian hacker who broke into Mark Zuckerberg's Timeline, but still won't reward him.
Khalil Shreateh, a Palestinian programmer found a Facebook bug that made it possible for people to post on a stranger's wall
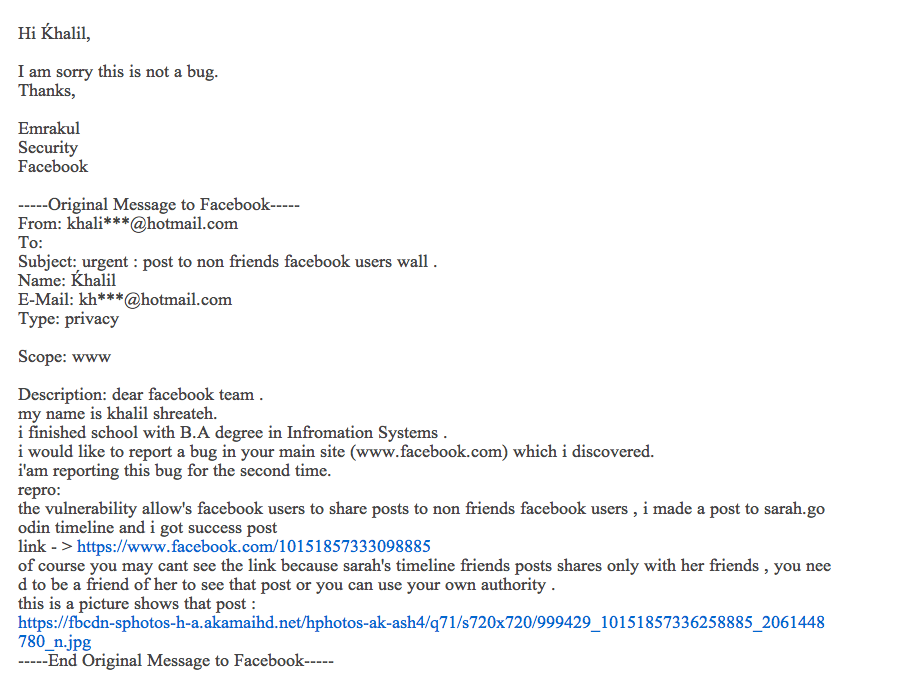
Days ago i discovered a serious facebook vulnerability that allows a facebook user to post to all facebook users timeline even they are not in his friend list. I report that exploit through whitehat --> www.facebook.com/whitehat
this email shows my report including facebook security replay : -
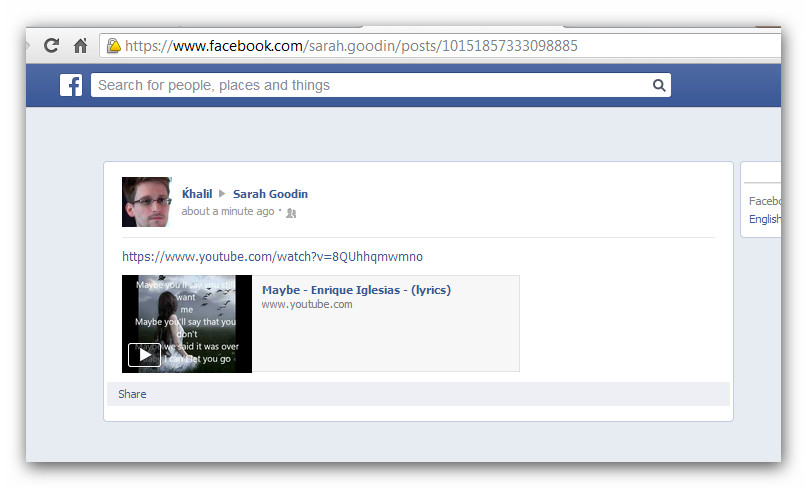
He tested this out by posting an Enrique Iglesias video on Sarah Goodin's wall (Mark Zuckerberg's friend)
Shreateh says he tested the vulnerability on Sarah Goodin — a friend of Facebook CEO Mark Zuckerberg, and the first woman to sign up to the service — before reporting it through Facebook's whitehat disclosure service for security researchers.
He emailed this bug through Facebook's 'White Hat' scheme, with the link to Sarah's wall but that didn't work out
Techcrunch says, "Unfortunately, the member of the Facebook Security team who clicked the link wasn’t friends with Goodin, whose wall was set to be visible to friends only."
A screenshot of Khalil's email to the Facebook security team, with the link to Sarah's wall but that didn't work out too well.
Image via imgur.comKhalil's blog says, "Facebook security replay was that the link gives error opening, of course they didnt use their authority to view Sarah's privacy posts as sarah share her timeline posts with her friends only."
Mr Shreateh said he had tried to use Facebook's White Hat scheme, which offers a monetary reward for reporting vulnerabilities, but had been ignored.
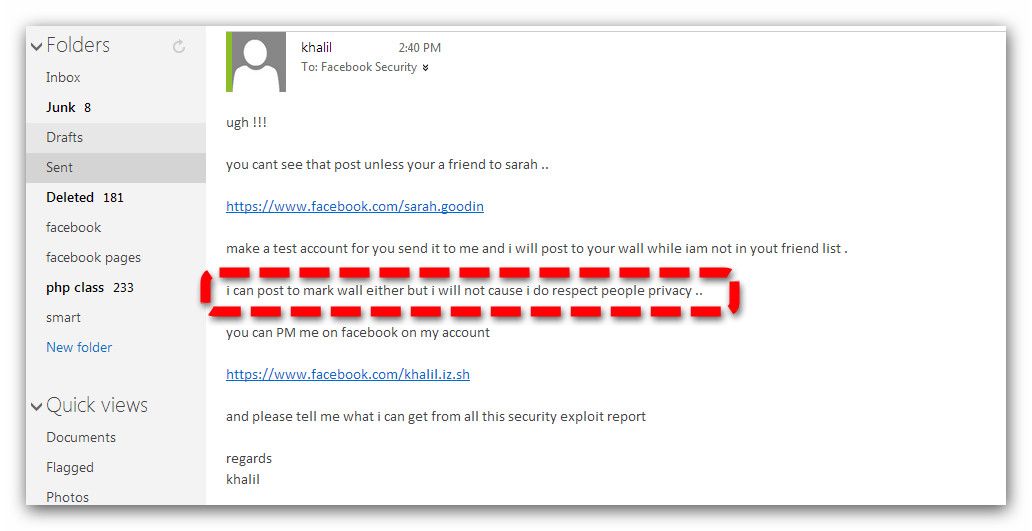
He sent another email saying that he could post it on Mark's wall but he wanted to respect Mark's privacy
The Facebook security employee who received the email — identified only as Emrakul — couldn't see the post, since he wasn't friends with Goodin. That's what Shreateh tried to explain in a follow up to Emrakul, warning that he could very well post to Zuckerberg's wall if he wanted.
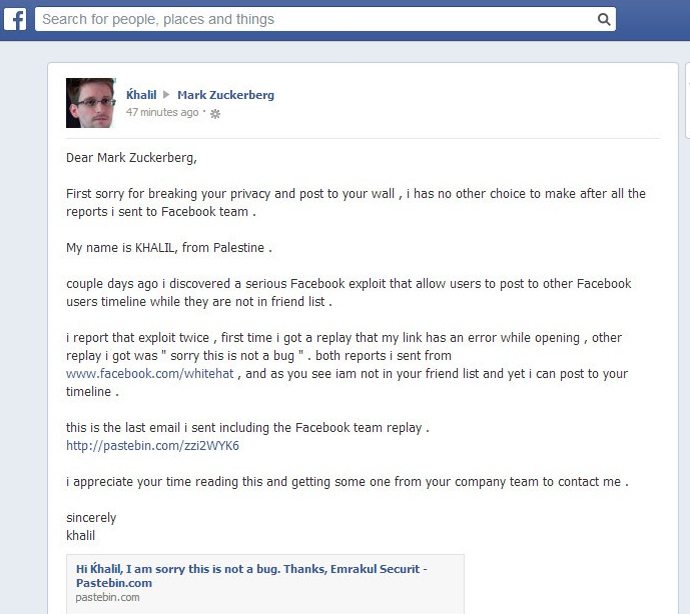
Image via blogspot.comHe didn't receive a response, so Khalil proceeded to prove his point by posting on Mark Zuckerberg's wall
He didn't receive a response, so Khalil proceeded to prove his point by posting on Mark Zuckerberg's wall
Image via geek.comShreateh then went on to explain his two failed attempts to work with Facebook's white hat security team — who pay hackers a minimum of $500 to find problems with the social network's site.
Needless to say, he finally got Facebook's attention but it came with a price instead of the $500 reward for 'White Hat' bug reports
Interviewd by Metro.us | When the social media profile of Mark Zuckerberg, the billionaire Facebook founder and global icon, was hacked by Khalil Shreateh, the ‘white hat’ hacker from the Occupied Palestinian Territories, the message posted was respectful.
A Palestinian hacker posted a message on Facebook CEO Mark Zuckerberg's page after he says the site didn't take his warnings about a security flaw seriously.
cnn.comThey temporarily suspended Shreateh's account and said they wouldn't pay him the bounty fee because, by posting to Zuck's account, he violated Facebook's terms of service.
 stuff.co.nz
stuff.co.nz
"We are unfortunately not able to pay you for this vulnerability because your actions violated our Terms of Service. We do hope, however, that you continue to work with us to find vulnerabilities in the site."
A Facebook engineer writes that the bug was fixed on Thursday and that the company should have asked for additional instructions after the researcher's initial report. But Facebook reiterated claims that Shreateh violated the company's TOS.
Facebook security team member Matt Jones wrote that the language barrier with Shreateh, who is not a native English speaker, and the volume of reports the site receives were partly to blame for the site's slow response.
"We get hundreds of reports every day. Many of our best reports come from people whose English isn’t great — although this can be challenging, it’s something we work with just fine, and we have paid out over $1 million to hundreds of reporters.
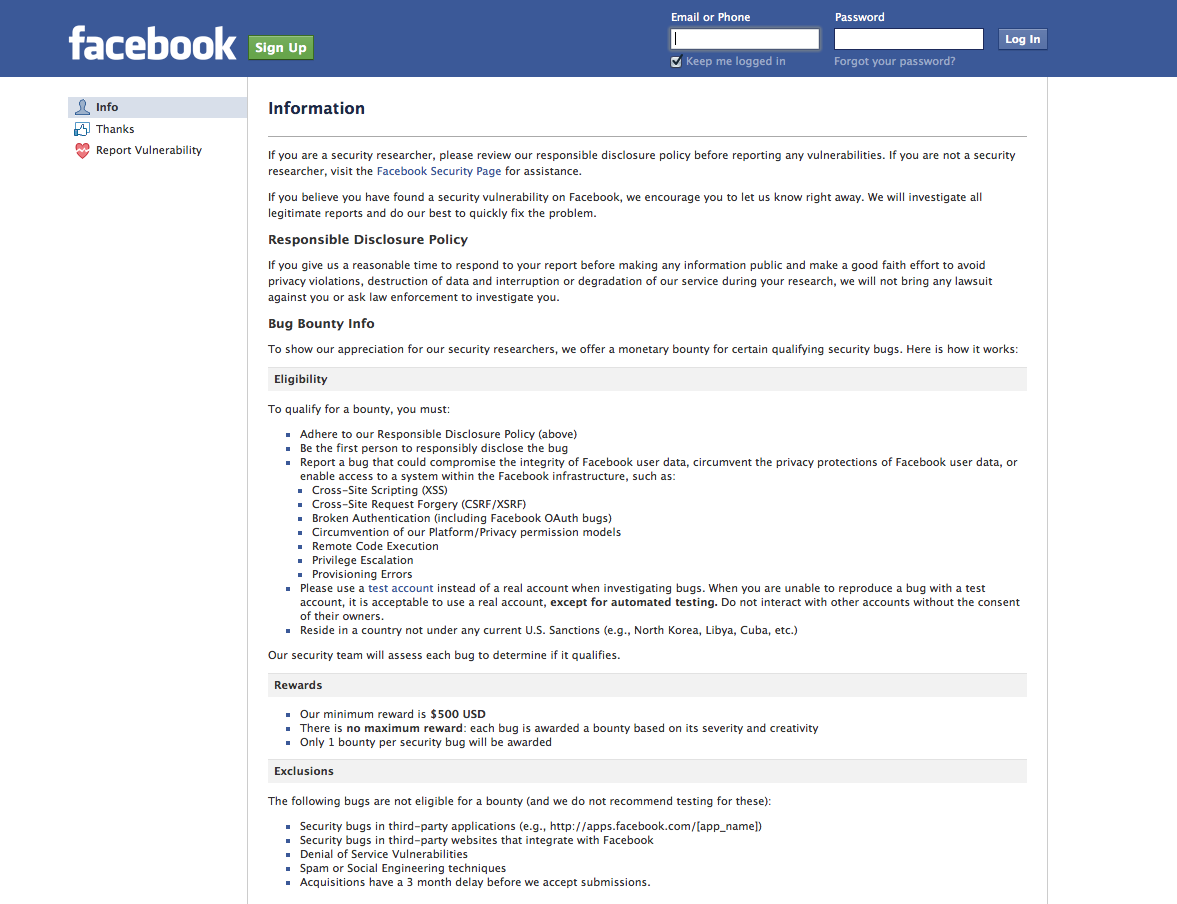
The 'White Hat' program on Facebook rewards programmers or security researchers $500 for reporting a bug
Facebook launched its bug bounty program in July, following in the steps of Mozilla and Google. The minimum a researcher can make for reporting a bug that is eventually confirmed is $500, and there is no maximum. Researchers have to follow Facebook's Responsible Disclosure Policy and not go public with the vulnerability information until the hole has been fixed.
Image via imgur.com“It is never acceptable to compromise the security or privacy of other people. In this case, the researcher could have sent a more detailed report (like the video he later published), and he could have used one of our test accounts to confirm the bug,” Sullivan writes.
Facebook says it will make changes to clarify the processes behind its whitehat program for reporting bugs.
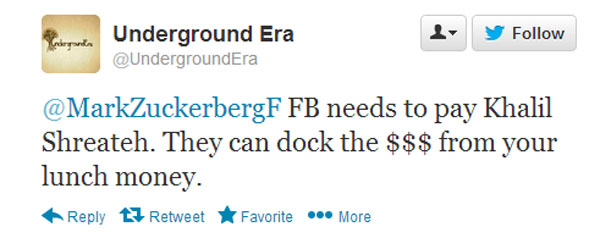
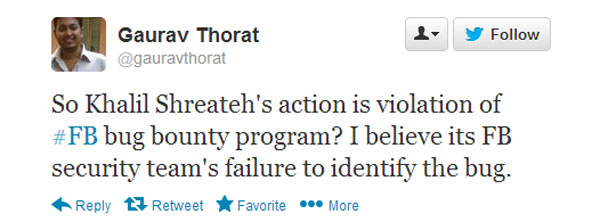
Some netizens say Khalil should have given more info, others say Facebook ripped him off
Some netizens say Khalil should have given more info, others say Facebook ripped him off
Image via everyjoe.comAfter Facebook refused to pay a security researcher the bug bounty he was hoping to get for a problem he reported with its service, a top security researcher has launched a campaign to pay the researcher money that Facebook denied him.
Commenters are split on whether Facebook ripped off Shreateh or not. Facebook says that Shreateh didn't include enough technical info when he tried to report it the bug. You can't just demonstrate the bug, you have to explain how it works.
 stuff.co.nz
stuff.co.nz
It’s ridiculous that this guy hasn’t been given a bounty payment. After getting ignored, he could have used his hack to wreak havoc. Instead, he remained white hat and simply did what was needed to get noticed. In our books, he’s a hero. Pay this man, Mark, we know you can afford it.
The support fund for Khalil Shreateh has almost hit $10,000! Even though Facebook was not willing to pay for his discovered bug due to the violation of rules, but netizens are already raising funds to support his career and help support his future researches.
This article on mashable.com got 2,000 shares in less than 5 hours | Facebook Hacker Breaks Into Zuckerberg's Timeline to Report Bug
Hacker News says, Palestinian Hacker posted vulnerability details on Zuckerberg’s Wall