The "WannaCry" Ransomware Attack Has Spread To Malaysia. Here's All You Need To Know
The attack, which locks computers and holds users' files for ransom, hit 200,000 victims in 150 countries over the weekend.
On Friday, 12 May, England's National Health Service was hit by a ransomware known as "WannaCry"
The massive attack shut down work at 16 hospitals across the United Kingdom.
According to The Guardian, the attack happened at roughly 12.30PM local time.
The ransomware threatens hospitals that they will lose access to patient records and other files if they don't pay money to the hackers.
By evening, the ransomware had spread to the United States, South America, Europe, Russia, and Taiwan
Car manufacturers like Nissan and Renault halted their production in several of their factories across the UK.
Other organisations hit include the Swedish engineering firm Sandvik, the German train operator Deutsche Bahn, FedEx, the Russian Interior Ministry, and several global telecoms companies.
Most recently, Malaysia and Singapore have been added to the growing list of countries hit by the attack
A digital directory service at Tiong Bahru Plaza in Singapore was affected by the WannaCry virus over the weekend.
A representative from the mall has confirmed to Channel NewsAsia that there was no sensitive information in the directories and that neither money nor bitcoins were paid to the hackers.
A real-time map of the attack puts Malaysia and Singapore as the countries affected by WannaCry.
CyberSecurity Malaysia, an agency under the Science, Technology and Innovation Ministry, has urged Internet users to be cautious with their machines
"We urge system administrators to patch their systems as soon as possible and keep their users aware of the new ransomware in order to prevent them from opening suspicious e-mails and files," said chief executive officer Datuk Dr Amirudin Abdul Wahab as quoted by The Star.
According to local IT security service provider, LGMS, at least 10 computers have been infected by the ransomware over the weekend.
How does WannaCry work?
Ransomware is a kind of cyber attack that involves hackers taking control of a computer system and blocking access to it until a ransom is paid.
The virus gets into a computer when a user clicks or downloads malicious files.
The user then gets a random demand which must be paid for access to be restored. Security experts warn there is no guarantee that access will be granted after payment.
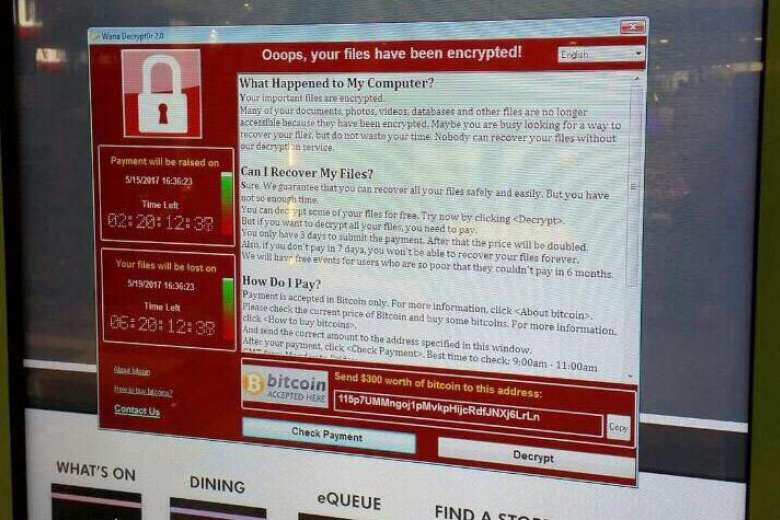
In the context of WannaCry, it primarily targets Microsoft's Windows operating system. A ransom of USD300 (RM1,300) - which is only accepted in bitcoin - must be paid to regain control.
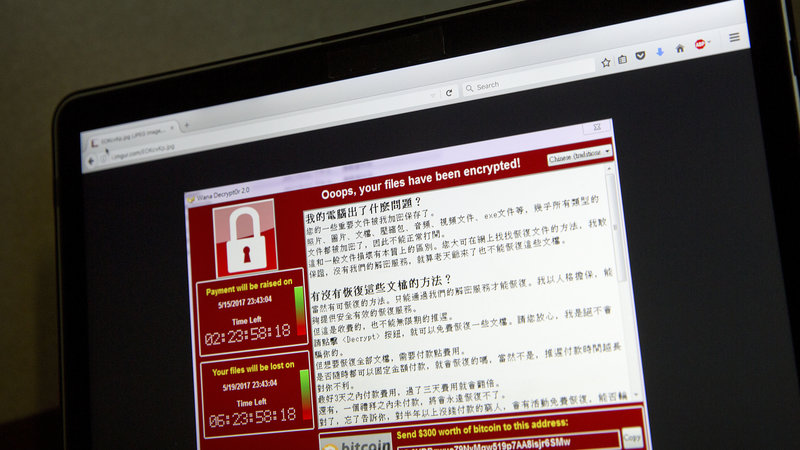
A screenshot of the warning screen ransomware attack, as captured by a computer user in Taiwan.
Image via APThe pop-up also features two countdown clocks; one showing a three-day deadline before the ransom amount doubles to USD600 (RM2,597) - another showing a deadline of when the target will lose its data forever.
WannaCry exploits a vulnerability in Microsoft, which released a patch to fix it in March.
However, people don't always install updates and patches on their computers and so this means vulnerabilities can remain open a lot longer and make things easier for hackers to get in.
Many are speculating that a hacker group is behind the attack and they've stolen a NSA-built device to aid them
A cyber gang - called "Shadow Brokers" - is being blamed for the hack. The mysterious organisation said in April it had stolen a "weapon" from the National Security Agency (NSA), America’s powerful military intelligence unit.
The hacking tool - known as "Eternal Blue" - gives unprecedented access to all computers using Microsoft Windows, the world’s most popular computer operating system.
A young 22-year-old cybersecurity expert known as "MalwareTech" slowed the attack by registering a domain name he discovered in the ransomware’s code, but he reckons that another attack is likely coming soon
The researcher, who identified himself only as MalwareTech, is a 22-year-old from south-west England who works for Kryptos logic, an LA-based threat intelligence company.
The threat receded when he found a "kill switch" that involves registering a domain name used by the ransomware.
Here's what you can do to protect yourself against the attack:
1. Install and use an up-to-date antivirus solution (such as Microsoft Security Essentials and Kaspersky).
2. Make sure your software is up-to-date.
3. Avoid clicking on links or opening attachments or emails from people you don't know or companies you don't do business with.
4. Install browser extensions that help identify reported phishing and malware websites.
5. Regularly backup your important files.