2 Million Facebook, Twitter And Gmail Account Passwords Stolen And Posted Online
More than 2 million accounts have been compromised from popular sites such as Google,Yahoo, Twitter, Facebook and LinkedIn after malware captured log-in credentials from users worldwide.
Nearly two million stolen usernames and passwords to sites like Facebook, Google and payroll company ADP have been stolen and posted online, a cybersecurity firm revealed Tuesday
A Russian-language website containing the compromised data was discovered by Trustwave, which blamed the breach on maliciously installed software that logged users' keyboard typing around the world.
Some of the other websites whose users were reportedly affected by the botnet, dubbed "Pony," are Yahoo, Twitter and Linked In.
nydailynews.comCybercriminals are using a botnet called Pony to steal account credentials Photo: iStock
Image via theage.com.auTwo Russian-speaking social networking sites were also among the most popular sites, possibly indicating that many of the victims are Russian speakers, Trustwave stated in a blog reporting their findings.
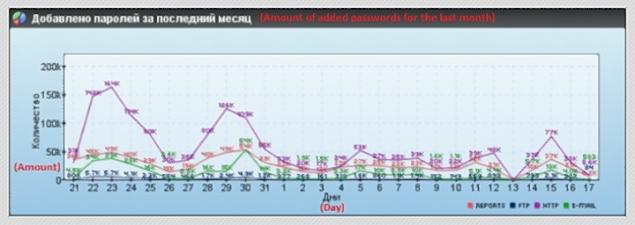
The number of stolen passwords by day are seen here, as reported by Trustwave
"We don't know how many of these details still work," security researcher Graham Cluley told the BBC of the stolen data. "But we know that 30-40% of people use the same passwords on different websites."
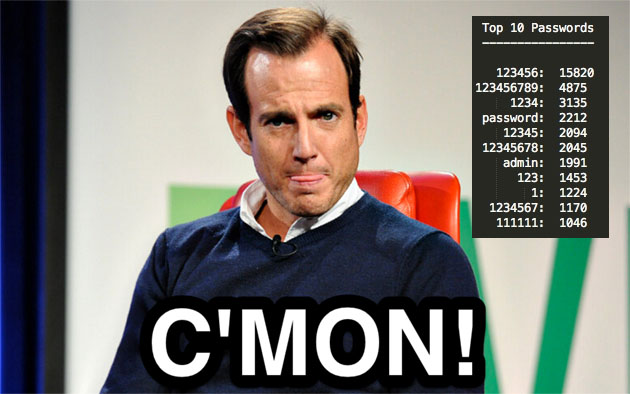
Trustwave reported the most common password in the database — used more than 15,000 times — was "123456."
nydailynews.comThe second most popular was "123456789", third "1234," and fourth, "password."
"That's certainly something people shouldn't do," said Cluley of these repeat and easy to guess passwords.
Commenting on the hack, Abby Ross, a spokesperson for Trustwave, said:
"Although these are accounts for online services such as Facebook, LinkedIn, Twitter and Google, this is not the result of any weakness in those companies networks."
"Individual users had the malware installed on their machines and had their passwords stolen. Pony steals passwords that are stored on the infected users' computers as well as by capturing them when they are used to log into web services."
cnn.comAlthough the culprit behind the hack remains unknown, Trustwave wrote on its blog that two targets were Russian-speaking social networking sites (vk.com and odnoklassniki.ru), which could hint at the virus' origin
"The malware was configured so that the majority of the credential information was sent to a server in the Netherlands," Ross said.
"The server does not show from which countries the information came from so we cannot break down exactly how many users from each country were affected. However, we can confirm the attackers targeted users worldwide including in the U.S., Germany, Singapore, Thailand and others."
 businessinsider.in
businessinsider.in
Trustwave reported the most common password in the database — used more than 15,000 times — was '123456.'
Image via nydailynews.comIt's also important to note that the stolen credentials were never publicly posted online. Trustwave researchers were able to access a command and control server used by the Pony botnet and recovered the passwords from there.
nydailynews.com"We have reached out to the major service providers affected and they are taking steps to inform their users or remediate the compromised accounts," Ross told Mashable.
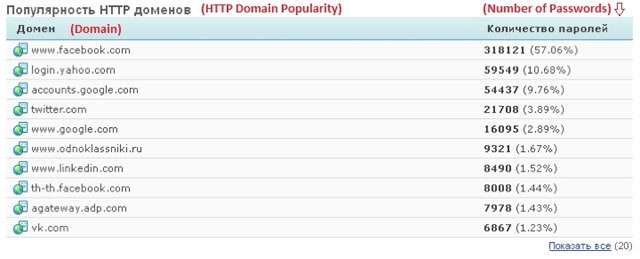
Facebook accounted for about 57% of the compromised accounts, followed by Yahoo (10%), Google (9%) and Twitter (3%)
A Facebook spokesperson told Mashable the company has already reached out to those with compromised accounts.
"While details of this case are not yet clear, it appears that people’s computers may have been attacked by hackers using malware to scrape information directly from their web browsers," a Facebook spokesperson told Mashable.
2 million passwords have been stolen, compromising accounts at Facebook, Gmail, Twitter, Yahoo and ADP.
Image via turner.com"As a precaution, we've initiated a password reset for people whose passwords were exposed." Facebook added that its users can protect themselves when using the site by activating login approvals and login notifications in their security settings.
"[These users] will be notified when anyone tries to access their account from an unrecognized browser and new logins will require a unique passcode generated on their mobile phone," the spokesperson said.
The company also discovered most of the compromised passwords were considered "weak."
cnn.com