Man Reveals How His US$50,000 Twitter Username Got Stolen Thanks To Paypal And GoDaddy
After reading how PayPal and GoDaddy allowed the attack and caused Naoki Hiroshima to lose his US$50,000 Twitter username, you would worry for your personal information too.
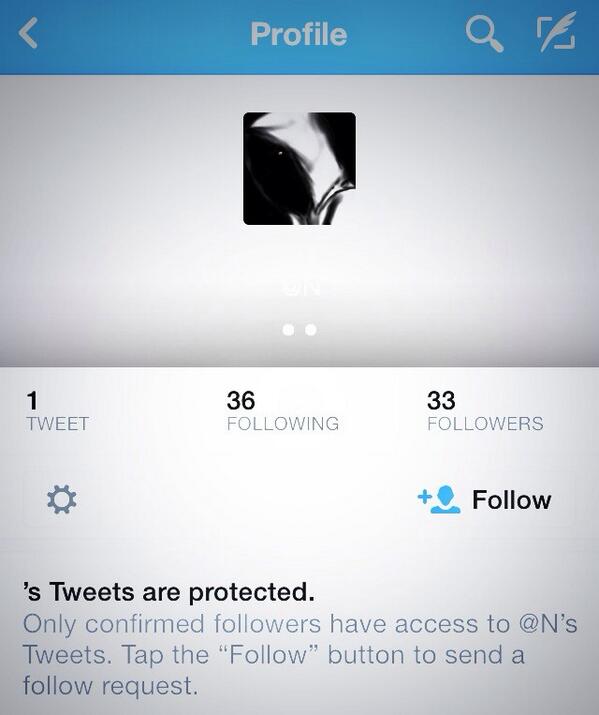
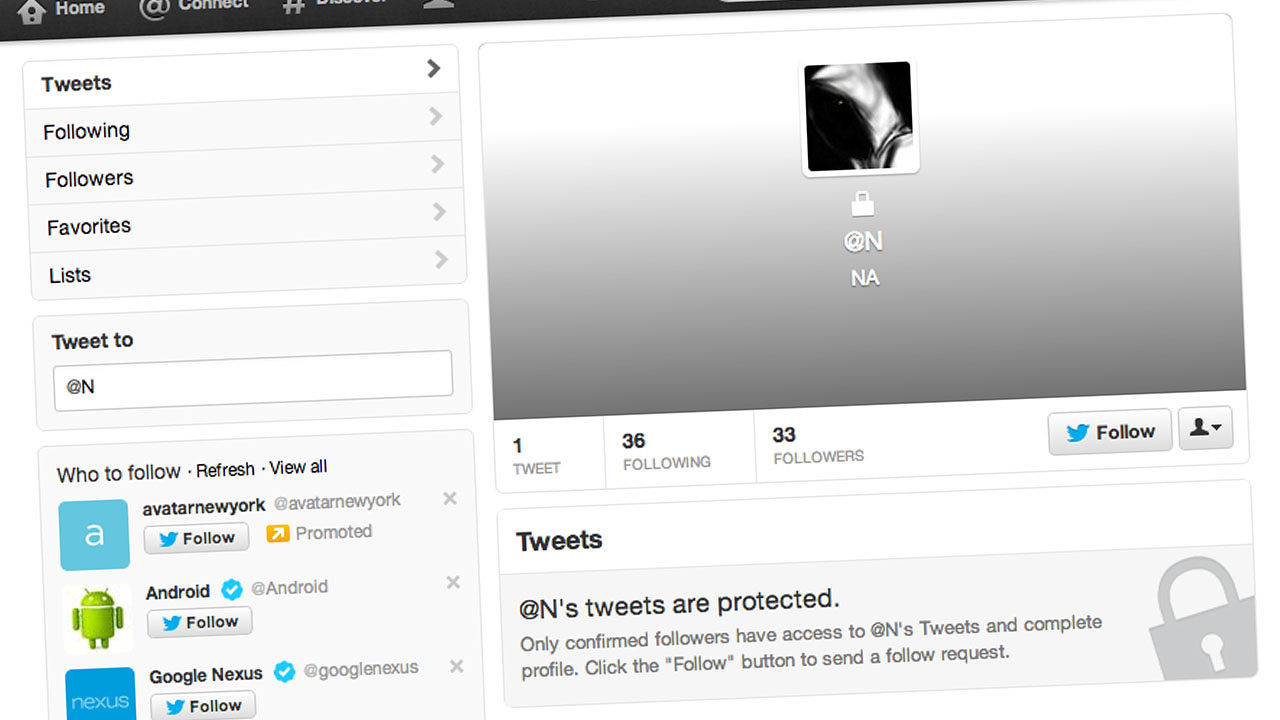
Naoki Hiroshima is a blogger and developer who, until very recently, owned the very rare 1-letter "@N" Twitter handle
The handle, which he had been offered up to $50,000 for in the past, was stolen after hackers abused security flaws in web hosting service GoDaddy and online payment gate PayPal to take control of Hiroshima's accounts, and extort him.
medium.comIn a detailed and dramatic post on blogging site Medium, Hiroshima explains how an attacker was able to steal the @N Twitter handle from him
Naoki Hiroshima, a developer of social apps like Echofon and Cocoyon, was used to people trying to steal his rare Twitter username, @N. He regularly received password reset instructions from people who were trying to gain control of his account, which he had acquired in 2007.
Once, he was even offered $50,000. He turned it down.
Ten days ago, an @N-coveting ne’er-do-well figured out a way to get Hiroshima to give up his Twitter handle.
cnet.comThe attack wasn't a simple one-layer exploitation; there was no hacker guessing that Hiroshima's Twitter password was "123456." Rather, this was a sophisticated multilayer attack that only worked because of human failure.
The would-be blackmailer, who goes by the moniker “Social Media King,” and uses an email address “[email protected],” began his attack by looking for leverage.
forbes.comHe noticed that Hiroshima had registered several domains through the GoDaddy domain registration service. He figured control of those domains could lead to control of @N.
medium.comIn a few simple steps, Social Media King circumvented the security measures of PayPal and GoDaddy. Within minutes. Hiroshima’s domains were his.
Here’s how the blackmailer, Social Media King did it:
First, he called PayPal. Posing as an employee, he persuaded another, real employee to provide the last four digits of Hiroshima’s credit card.
forbes.comNext, Social Media King called GoDaddy. He told them he had lost his credit card, but that he remembered the last four digits.
medium.comGoDaddy then let the attacker guess the first two digits of the card. He did so correctly, and GoDaddy gave him access to Hiroshima’s account.
cnet.comOnce Social Media King was in, he changed all Hiroshima’s account information.
forbes.comHere's what happened next:
As part of GoDaddy’s security practices, the company duly informed Hiroshima that his account settings had changed. Hiroshima called GoDaddy to explain the situation.
But he was confounded when the representative asked for the last six digits of his credit card to confirm his identity. Unfortunately for Hiroshima the Social Media King had already changed the credit card number. Hiroshima was now nobody as far as GoDaddy was concerned.
By taking over Hiroshima’s GoDaddy accounts, Social Media King was also able to take over his email and his Facebook account
Friends began to alert Hiroshima that his Facebook account was acting funny. But @N was linked to a email address that Social Media King did not control. It was still out of reach.
forbes.comIn the mid-afternoon of January 20, Social Media King sent a blackmail note to Hiroshima:
“I would like to inform you that your GoDaddy domains are in my possession, one fake purchase and they can be repossessed by GoDaddy and never seen again D:"
medium.com“I see you run quite a few nice websites, so I have left those alone for now, all the data on the sites has remained intact. Would you be willing to compromise?"
"Access to @N for about 5 minutes while I swap the handle in exchange for your GoDaddy and help securing your data?”
forbes.comHiroshima pondered the request for a few hours. Finally, he concluded “giving up the account right away would be the only way to avoid an irreversible disaster.”
Naoki Hiroshima then released US$50,000 twitter handle @N.
medium.comIn exchange, the attacker helpfully provided some tips to Hiroshima so that he could avoid becoming a victim in the future
First, he suggested calling PayPal and asking an agent to add a note to his account not to release details over the phone.
forbes.comSecond, he suggested switching to a more secure registrar like NameChap or eNom.com.
Looking back, Hiroshima has some suggestions of his own
Hiroshima advises not using emails based on custom domains (like [email protected]) to log in to service you value. If the registrar of those domains is compromised, then you can kiss the security of your emails goodbye.
It is can also be helpful to protect particularly sensitive data with two-factor authorization, which requires a user to enter both a password and a special code that is sent to his or her phone.
forbes.comFinally, Hiroshima urges making a technical change to your mail server records that would delay the time it took for a change to take effect. Time is the enemy of the digital attackers. The longer it takes to pull off a heist, the most exposed an attacker becomes.
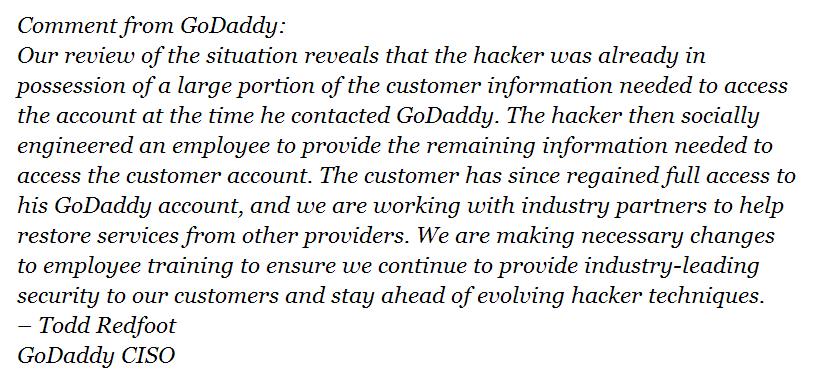
nydailynews.comIn response to questions from various media houses about Hiroshima’s story, this is what PayPal, GoDaddy and Twitter said:
In response to reporters’ questions about Hiroshima’s story, @Ask PayPal tweeted “our investigation did NOT disclose any credit card details. More info soon.”
forbes.comTwitter said it is investigating but does not comment on individual’s accounts. It’s worth noting that Twitter appears to have banned the @N account at the time of this writing, so the gears are turning.