While Five Million 'Gmail Passwords' Were Leaked, Here's Why You Shouldn't Panic
Nearly 5 million usernames and passwords associated with Gmail accounts have been leaked on a Russian Bitcoin security forum. Here's everything you need to know about it.
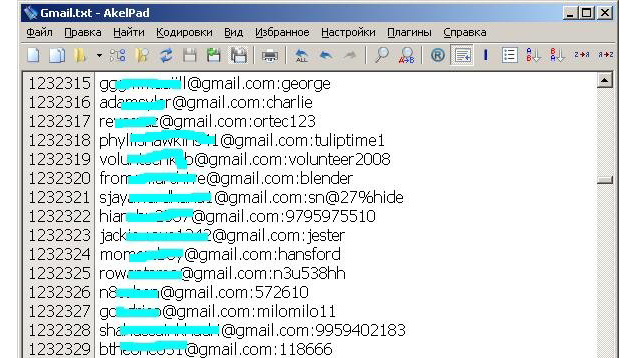
Earlier this week, almost five million combinations of Gmail addresses and passwords were posted in a Russian Bitcoin forum
The list has since been taken down, and there's no evidence that Gmail itself was hacked—just that these passwords have been leaked.
 lifehacker.com
lifehacker.com
Some people who checked the list and found their Gmail addresses there reported that it contained an old password for them, and often a password that they had reused on multiple sites.
forbes.comGoogle itself says less than 2% of the leaked address-password pairs were current for Gmail. That sounds small but it means nearly 100,000 people need to change their Gmail passwords ASAP. If you’re one of them, Google should have already notified you.
forbes.comAccording to some of the leak's victims as well as security experts, many of the passwords were taken from websites where users used their Gmail addresses to register
For example, someone might have signed up for a website with the username "[email protected]" and the password "mypassword." The list exposed this week makes it look like "mypassword" is the password for the Gmail account itself, but the user's actual Gmail password might be totally different.
While SAYS is unable to confirm the authenticity of all the email addresses on the list, Mashable reports that one of its employee saw that his old and unused Gmail password is part of the leak
A screenshot showing Mashable employee's old password is part of the leaked database.
Image via mshcdn.comAccording to a Google, they've "no evidence that our systems have been compromised," and security experts seem to agree that the passwords are either old Gmail passwords obtained through phishing, or are passwords that were actually used on other sites
That gmail dump looks very old folks. Can confirm a dummy account w/ password that was already changed twice. Dump has original pw.
— Ben Ten (0xA) (@Ben0xA) September 10, 2014
@troyhunt I don't think this dump originates from gmail/Google. It's most likely compiled from multiple sources
— Janne Ahlberg (@JanneFI) September 10, 2014
Matteo Flora, a computer security expert, reviewed the dumped file and found that around 60 email addresses were in his address book. After he alerted those people, 30 of them told him that the password either was never used for their Gmail accounts or was very old, Flora told Mashable.
Chester Wisniewski, a senior security adviser for security firm Sophos, told Mashable that he expects many of these accounts not to be valid. "There is no honor among thieves as they say, and often stunts like this are released as a sad attempt at gaining credibility among other criminals," he said.
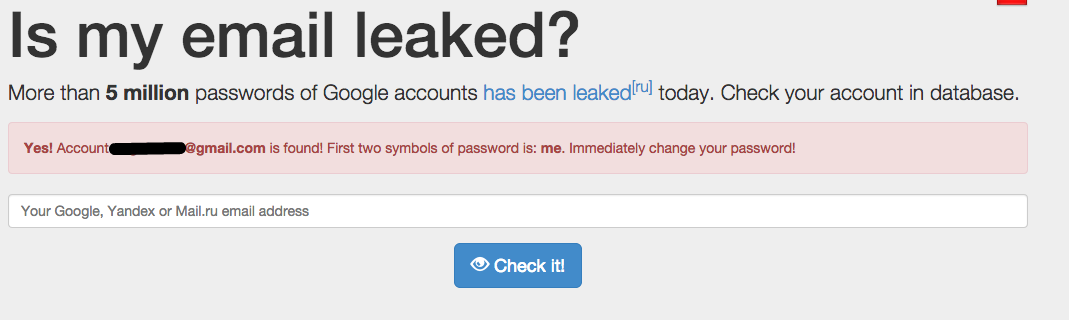
Meanwhile, a site IsLeaked.com that tells you if your email is in the leak, as well as the first two letters of the password, should NOT be used. As it might be a trap to collect email addresses.
For the love of god, Don't go to IsLeaked, there is a good chance that's a scam http://t.co/o0s1uMByUM
— George Mauer (@togakangaroo) September 11, 2014
A site — IsLeaked.com — to check if your address is in the leak immediately popped up. Blogger James Watt points out that the site was created September 8, the day before the list was posted to the Bitcoin forum, and is warning people not to use it, saying it might be a honey pot to collect email addresses.
“We just found .txt file with logins and passwords and made a service,” the anonymous person behind IsLeaked told me in an email. He says he created the site after a massive leak of Russian mail service Yandex addresses that happened on September 7, and that he simply added Gmail to the mix when it coincidentally happened after. “There is no conspiracy theory,” he says by email.
forbes.comIf you’re nervous about handing your email address over to the site, you can also check it on HaveIBeenPwned, a data breach check site run by Australia-based software engineer Troy Hunt, or on a leak tester that runs locally, but neither will tell you the password associated with the account.
forbes.comGoogle encourages people to chill out about the leak. "We're always monitoring for these dumps so we can respond quickly to protect our users," says Google's security team.
“We found that less than 2% of the username and password combinations might have worked, and our automated anti-hijacking systems would have blocked many of those login attempts. We’ve protected the affected accounts and have required those users to reset their passwords.”
Finally, what if the list of usernames and passwords doesn't get posted to a public forum where Google can spot it? This is why 2-step verification is a good idea.
Make sure you’re using a strong password unique to Google. Update your recovery options so we can reach you by phone or email if you get locked out of your account. And consider 2-step verification, which adds an extra layer of security to your account. You can visit g.co/accountcheckup where you’ll see a list of many of the security controls at your disposal.
Google also says it’s constantly monitoring accounts for unusual activity. “We’ll stop sign-in attempts from unfamiliar locations and devices,” the security team writes. “You can review this activity and confirm whether or not you actually took the action.”
forbes.com